Upgrade an Azure app to use Microsoft Graph
If you already have an Azure application and you want to upgrade it to use Microsoft Graph (for example, to use integrations like Microsoft Teams), follow the instructions on this page.
Add Microsoft Graph scopes
First, add the Microsoft Graph scopes that you need to your Azure application:
-
From the Azure Portal home page, select Azure Active Directory in the left navigation menu.
-
Click App registrations.
-
Choose the application that you want to configure.
-
On the left side of the page, click API permissions.
-
Click Add a permission > Microsoft Graph.
-
Depending on the Nylas features you're using, add the following permissions:
- Email messages — Read only:
Mail.Read - Email messages — Read and Write:
Mail.ReadWrite - Send email messages:
Mail.ReadWrite,Mail.Send - Calendar — Read and Write:
Calendar.ReadWrite - Contacts — Read only:
Contacts.Read - Contacts — Read and Write:
Contacts.ReadWrite
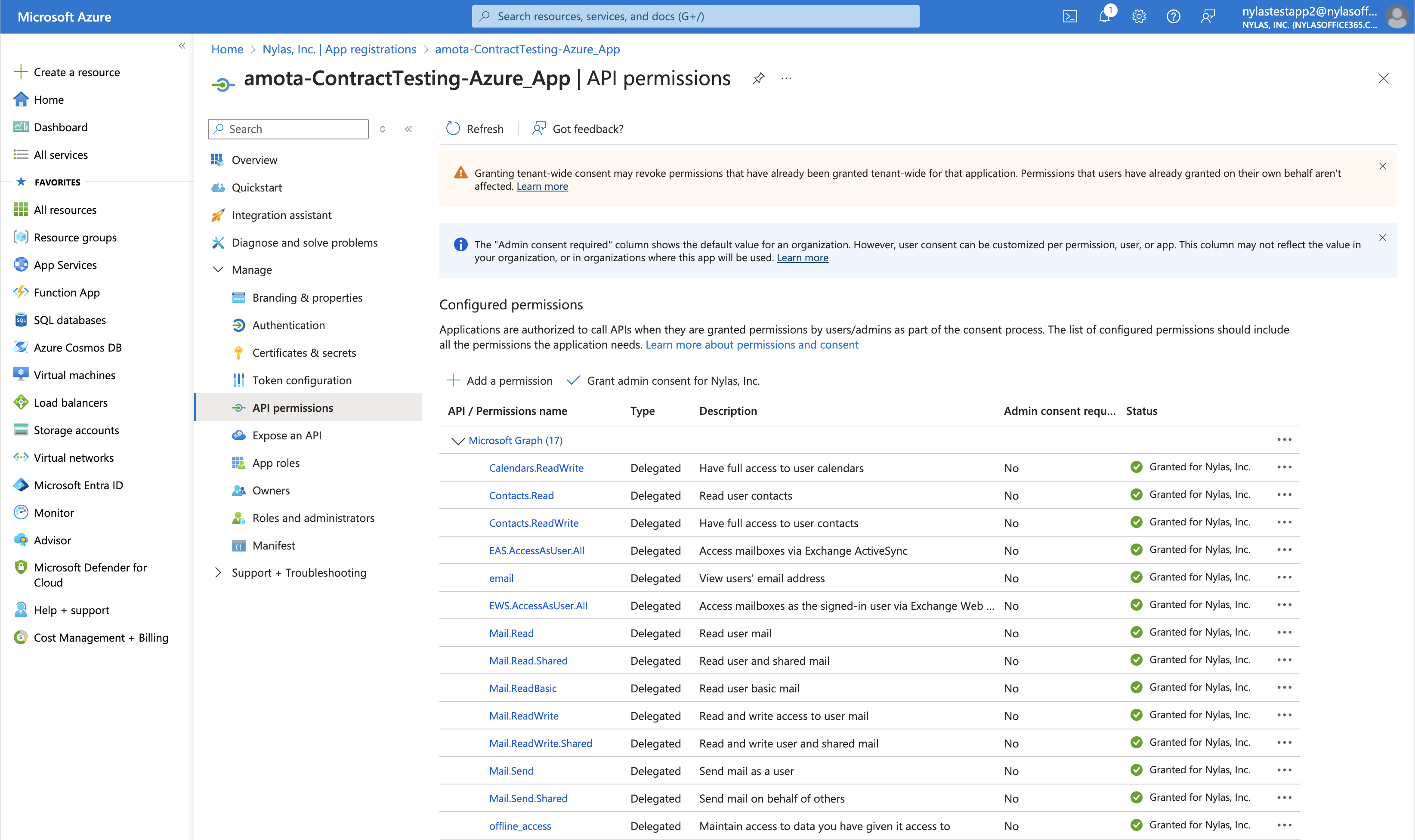
- Email messages — Read only:
-
(Optional) If you're using integrations (for example, Microsoft Teams), click Delegated permissions and use the search bar to find and add
OnlineMeetings.ReadWrite.
Confirm that you've requested all the correct scopes before you continue. These scopes are what switch your Azure app to using Microsoft Graph.
⚠️ Be sure to keep your existing Exchange Web Services (EWS) and Exchange ActiveSync (EAS) scopes. Nylas is migrating services to Microsoft Graph in phases. Your Azure app might experience interruptions if you remove your existing EWS or EAS scopes. You'll receive an update from Nylas when you can remove these scopes.
Re-authenticate end users
After you select the Microsoft Graph scopes, you must re-authenticate your end users to add those scopes to their accounts. You have two options to do so:
- Force your end users to re-authenticate their accounts.
- Communicate the changes to your end users and ask them to re-authenticate.
Add redirect URIs to your Azure application
Next, add redirect URIs to your Azure application:
- From the Azure Portal home page, select Authentication in the left navigation menu.
- Click Add a platform > Web.
- Add a redirect URI. Nylas requires a redirect URI to complete the authentication flow for your end users. The URI that you use depends on your location.
- If you're in the U.S., use
https://api.us.nylas.com/v3/connect/callback. - If you're in Europe, use
https://api.eu.nylas.com/v3/connect/callback.
- If you're in the U.S., use
- Click Configure.
- Scroll down to the Implicit grant and hybrid flows section and check the following options:
- Access tokens: This is used for implicit flows.
- ID tokens: This is used for implicit and hybrid flows.
- Save your changes.
- Scroll down to the Supported account types section and choose which type of application you're using.
- If you need to limit authentication to only accounts from your organization, choose Single tenant. You'll need your tenant ID for this option, and you must MDM verify your app before you can publish it.
- If you don't need to limit authentication to your organization, choose Multitenant.
- Click Save.
Get your Azure client secret and value
💡 If you already have your Azure client secret and value, you can skip this step.
Finally, get your Azure client secret and value:
- From the Azure Portal home page, click Certificates & secrets in the left navigation menu.
- Click New client secret.
- Fill in the description and select the duration that you want the secret to be valid.
- Copy the value and keep it somewhere safe, like a secrets manager. For best practices, see Storing secrets securely.