Authentication in Nylas v2
Nylas integrates with 100% of email, calendar, and contacts providers, and supports several authentication types. This includes modern OAuth authentication for Google and Microsoft accounts, and secure password authentication for legacy servers.
Nylas also supports identity providers (IDP) with single sign on (SSO) capabilities like Okta and OneLogin. If your customers require SSO for their Office365 or GSuite accounts through a third party IDP, you can authenticate these accounts with no additional set up steps as long as you use OAuth authentication. See the Microsoft Authentication Guide and Google OAuth Setup Guide for more information.
Nylas provides two authentication types to sync email, calendar, and contacts account data: Nylas Hosted Auth and Native Auth.
Choose an Authentication Method
Nylas saves you time by simplifying the process of securely authenticating different types of email accounts, and with minimum effort for end users. Nylas offers two different ways to authenticate accounts based on your application’s requirements: hosted authentication (Nylas handles the entire process) and native authentication (full customization with authentication information submitted to Nylas).
Hosted authentication
Nylas Hosted Authentication is the simplest to implement, and the most recommended method. In hosted authentication, Nylas handles the entire process so you can get to market quicker.
With hosted authentication, Nylas handles the entire authentication flow, including provider detection, server settings detection, OAuth, Single sign-on, credential collection, and credential storage. Nylas also offers options to customize the hosted authentication experience to brand it as your own.
When you use hosted authentication, you redirect users to a Nylas login page. Nylas detects the third-party providers, provides the correct login screen, and manages token exchanges for the user account.
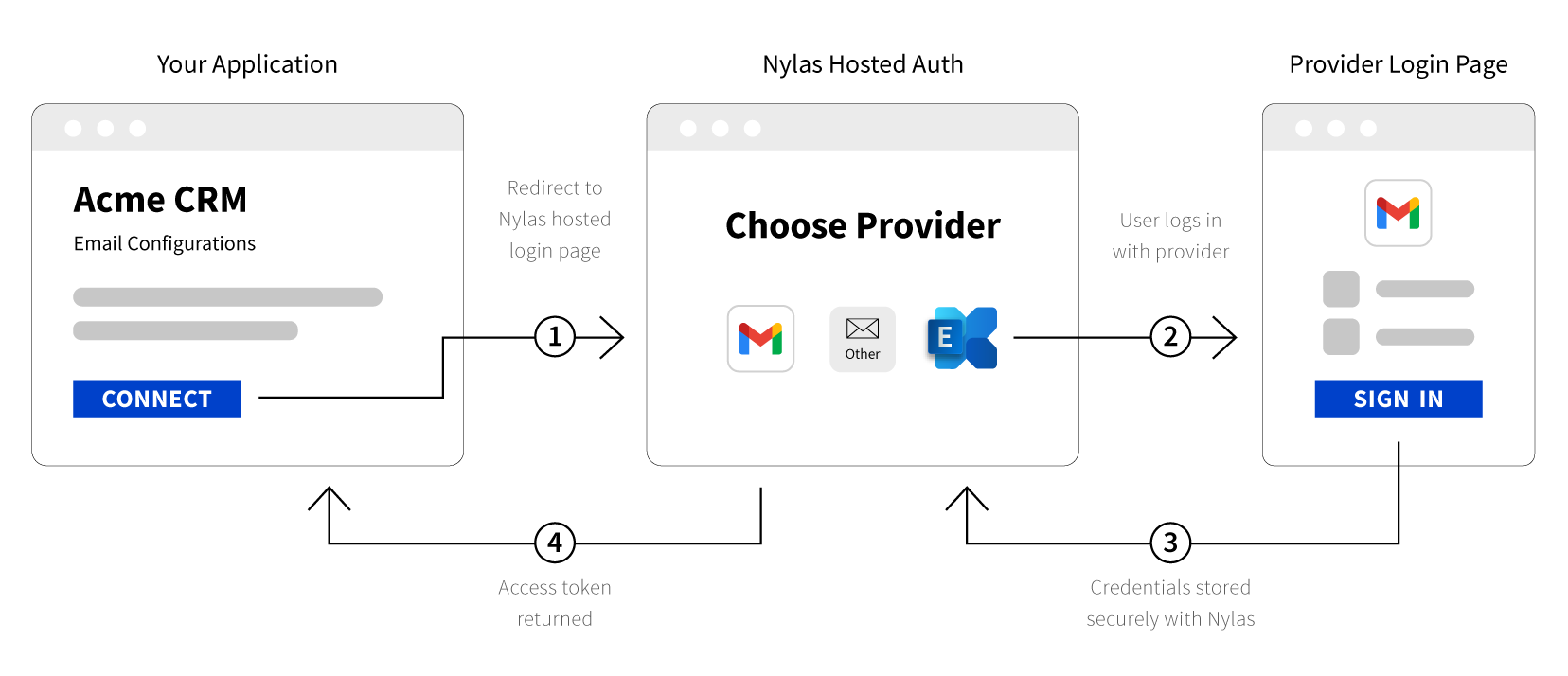
The basic hosted authentication flow process is as follows:
- You create a custom URL that redirects users to Nylas hosted authentication.
- A user clicks the link, and signs in to their account. This gives your application permission to access their account with the scopes you requested.
- After authenticating, Nylas redirects the user to your application with a one-time-use code.
- Your application exchanges the one-time-use code for an access token that it can use to access the Nylas APIs on the user's behalf.
To enable OAuth for Google and Microsoft 365 through hosted authentication, you must first create an application for each provider, and save credentials to that application in the Nylas developer dashboard. See the Google provider integration guide and the Microsoft provider integration guide to learn more.
Single sign-on is automatically supported when you use OAuth to authenticate accounts. Nylas supports all other email providers, including IMAP providers, with no prior configuration.
Learn More
Learn more about Hosted Authentication
Native authentication
Nylas native authentication is for developers who want to completely customize the authentication experience to perfectly match their app. With Nylas native authentication, the users authenticate directly in the app without redirecting to the Nylas Auth service, so this method can completely hide Nylas from your users. This gives you as the developer full control over the process, look and feel of the login experience, and allows you to control which kinds of providers the application supports.
If you use native auth, you must first set up developer apps with the third-party providers you use (for example Google and Microsoft), then configure your application to perform all the authentication and credential management tasks required. This is much more complicated than hosted authentication, so Nylas only recommends it for developers who require that level of customization control.
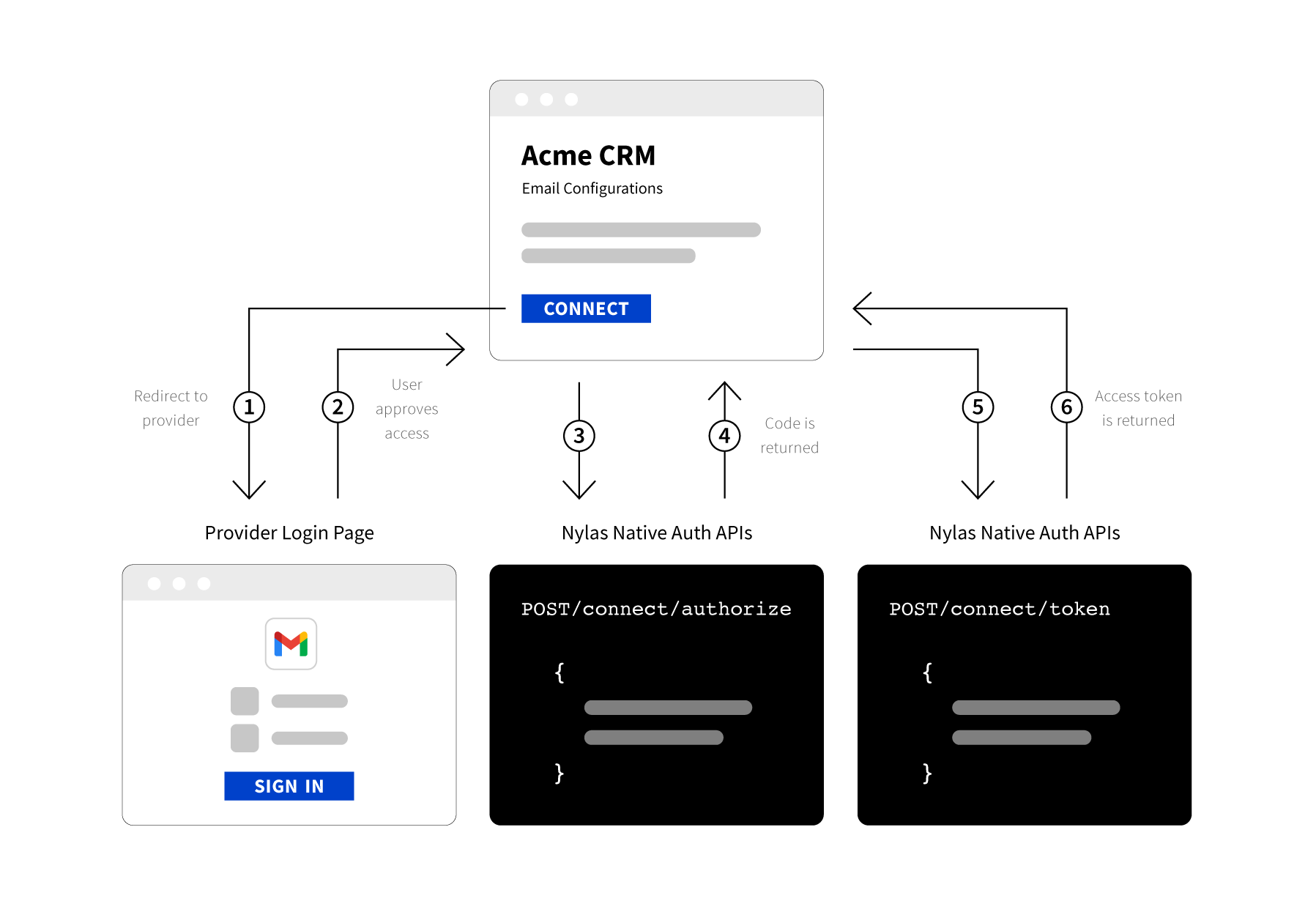
The native authentication guide explains the process of setting up this method.